- You need help? +593 4 2490070
6 security risks in WhatsApp and how to avoid falling into fraud
It is no coincidence that more frauds are committed through WhatsApp every day. Its popularity among all is so great that cybercriminals have found a new way to commit their scams. It is free, easy to use and allows you to contact family and friends through private messages, group conversations and stories, mass dissemination of information to contacts, calls, video calls or sending files.
| This application has been on the market for more than a decade and although it insists on affirming that security is part of its DNA, there are some risks (specific to the app and not) to which users are exposed when using it. In this post we collect them for you. Take notes and letters on the matter! | +2.000millions of users in the world use WhatsApp. (Whatsapp, 2020) |
1. Smishing
It's the turn of the well-known smishing! This is another social engineering attack that you can be a victim of through WhatsApp.
It is a variation of phishing, since this attack is carried out through text messages or WhatsApp. The attacker impersonates a company you trust and requests sensitive data to solve a problem, give you a prize or offer you discounts. It is also possible that you attach the link to a website. Don't click! It is a fraudulent website created and managed by cybercriminals to extract your information and access bank accounts.
Our advice
Never give access credentials to platforms and accounts through this application or any other. Remember that at Banco Pichincha we do not request this personal information through messages, calls, e-mails or social networks.
2. Extortion and identity theft
Security gaps in the digital environment and, in this case WhatsApp, allow unauthorized access, theft and kidnapping of information and sensitive data of the victims. So another risk users are exposed to is extortion linked to identity theft.
Many, under insistence, deception or intimidation, are forced to hand over access credentials or money. In Ecuador, these cases are quite common, so below we will review some ways of operating that cybercriminals have.
- They pose as an acquaintance who asks for support to retrieve goods at customs.
- They impersonate a family member or friend to request help to retrieve luggage during a trip and obtain money.
- They pose as a relative who has erroneously requested a password to be sent to the victim's cell phone number. If it sends you the code, the attacker obtains the history of conversations and WhatsApp files, among which there may be credentials and bank accounts.
- They contact the victim and ask for a cash reward in exchange for private photos and videos that have been kidnapped.
- They impersonate a trusted company with which the victim has a relationship, to collect a fictitious debt and pressure her to disburse money.
- They impersonate a financial advisor by requesting the update of data and thus seize the victim's bank accounts.
Our advice
Never give access credentials to platforms and accounts through this application or any other. Remember that at Banco Pichincha we do not request this personal information through messages, calls, e-mails or social networks.
3. Attacks from public networks
If you have read our content on cybersecurity before, you will know that surfing the internet using public networks is always a very bad idea. If not, now we explain it to you.
The problem when browsing the internet with a public network connection from your computer or cell phone is that they do not encrypt the information you transmit with each click you make, so anyone with hacking skills could have access to your personal data.
Although this is not a WhatsApp problem, your user in this application can be compromised when using public networks. How? Thanks to the 'middle man attack' or man-in-the-middle. This means that the cybercriminal intercepts all the information you generate on the internet to use it in their favor; for example, your WhatsApp profile and all your messages. Never use public networks!
Our advice
If you are forced to use these unencrypted networks, avoid opening WhatsApp Web. Never give usernames and passwords to anyone through this channel, not even to your parents!
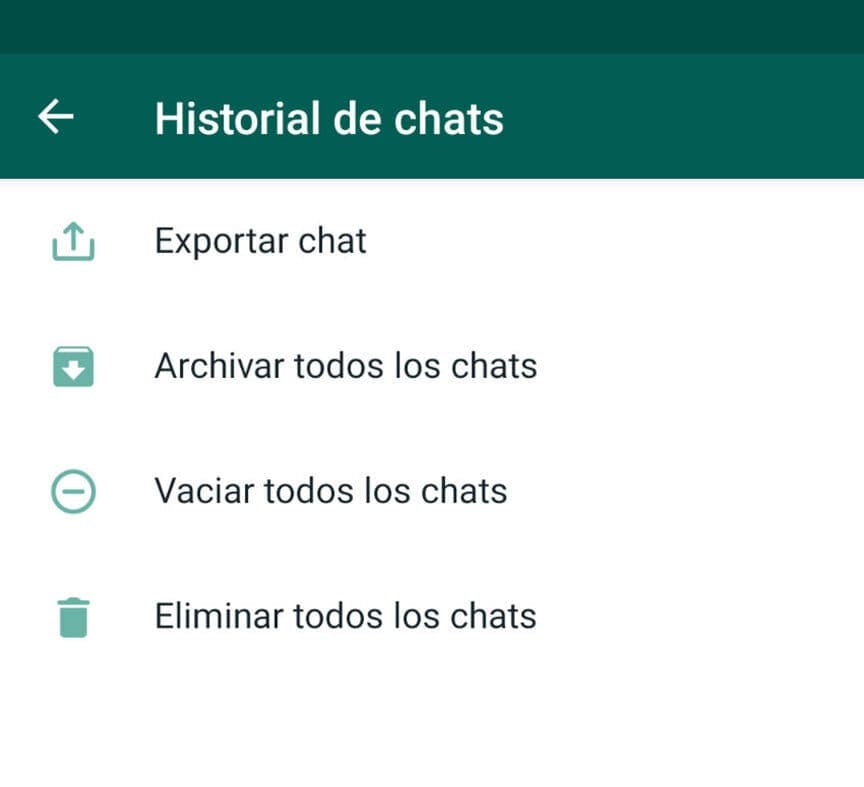
Conversations on WhatsApp can be exported. Try to delete all chats periodically.
4. Theft of messages and backups
Let's be honest, it is common to make purchases via WhatsApp by handing over your debit or credit card details. It is also common that, in a moment of urgency, we entrust the Web Banking credentials to a family member to carry out a transaction. You can delete those messages with sensitive information but that's not enough. Why?
Although WhatsApp allows you to delete the messages you send, both for you and for the recipient, they are actually stored in a sort of recycle bin in a database management system called SQLite. This database is decryptable, so anyone with the necessary knowledge and tools can obtain information from you that you thought no longer existed.
On the other hand, WhatsApp backups, more than a help for the user, can mean a security breach. With your email, the cybercriminal can retrieve them and use the information as best suits him. Are you sure you didn't send passwords through this channel?
Our advice
To delete the messages permanently, you can delete the application and reinstall it. Also, avoid making backup copies.
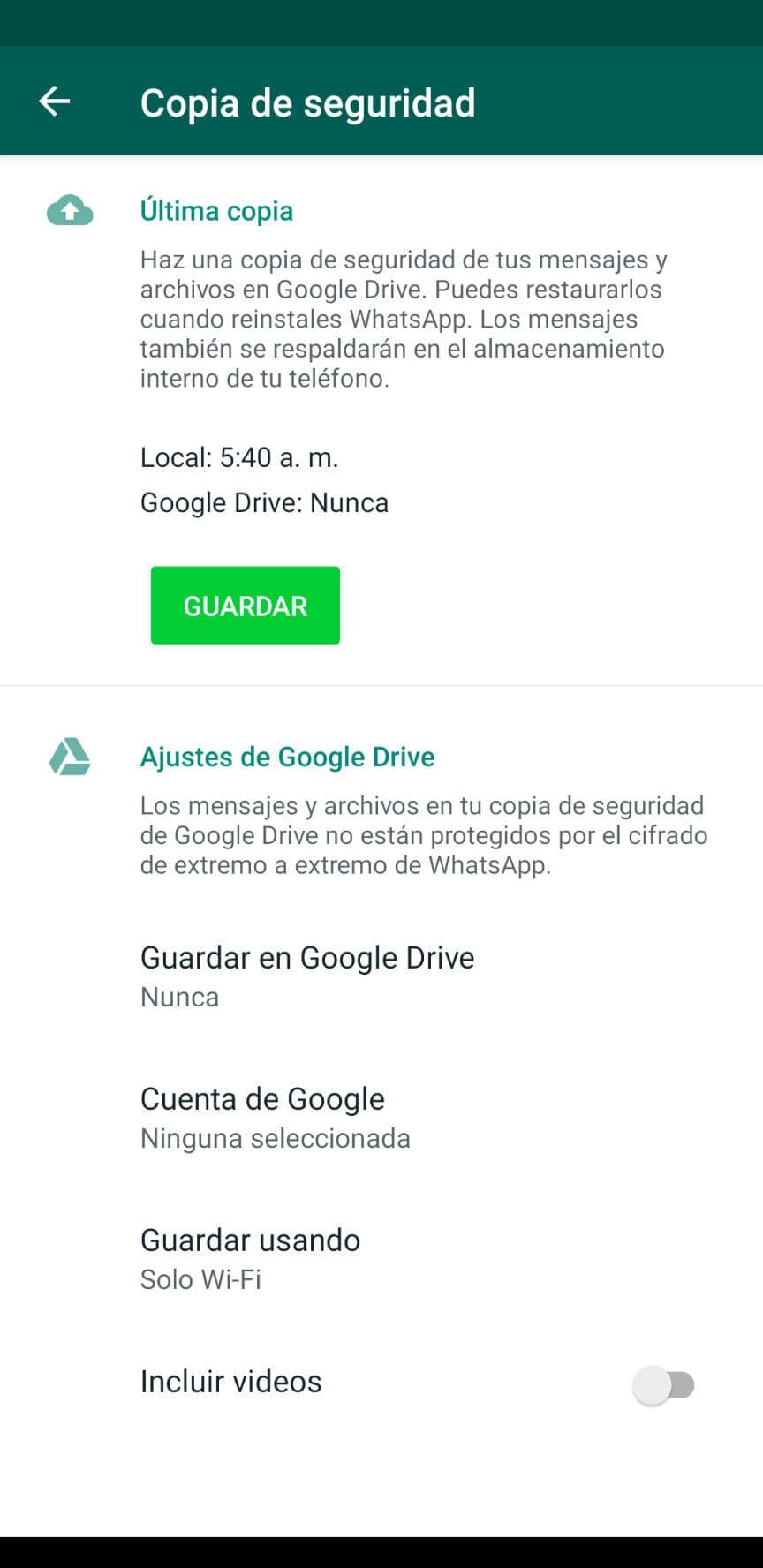
Find the backup settings in the 'Chats' section in WhatsApp Settings.
5. QRLJacking (Quick Response Code Login Jacking)
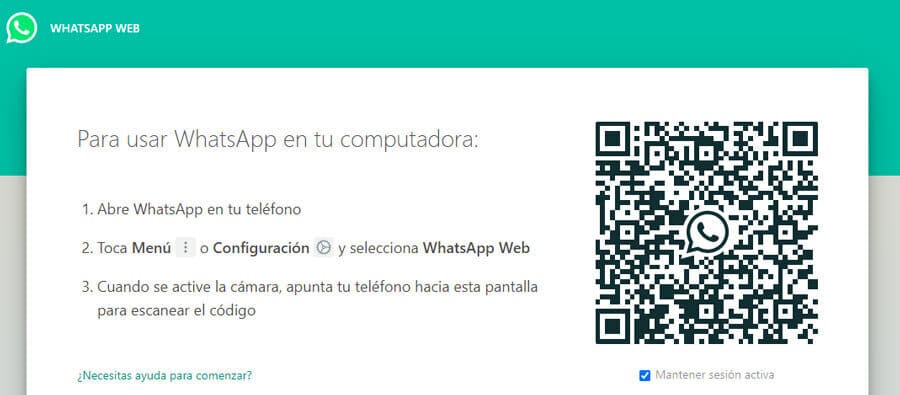
Before logging in to WhatsApp Web, deactivate the option to keep the session active.
This is a type of social engineering attack that consists of the violation of the QR codes generated by mobile applications, to offer functionalities to users. In this case, WhatsApp uses QRs to log into its web version. Keep reading, we will explain it to you in detail!
The QR code is a kind of image that privately stores several encrypted codes never visible to users. It works like a barcode, the kind that we see on product packaging and that also store information.
Cybercriminals take the image of the QR code delivered by the app to access WhatsApp Web and place a new encrypted code created by them. In this way, when the user logs in, the attacker has already stored his access data. From there, you can use the victim's account. All your conversations, photographs, images and videos that have been sent by this channel will be in your hands. Can you imagine the fate they may have?
Our advice
Check and close your WhatsApp Web sessions periodically. Activate the double authentication factor to keep your accounts protected.
6. End-to-end unencrypted payments
In some countries, WhatsApp has the option of direct payments from the application enabled and, although this functionality is not active in Ecuador at the moment, we provide you with information about this type of cybersecurity risk. Pay attention to our advice! Do you remember the end-to-end encryption that WhatsApp applied to all conversations? This is a communication system that encrypts messages, allowing only the sender and receiver to see them. This security method basically ensures that you are not the victim of a man-in-the-middle attack. Now, let's get back to payments. | 49%of purchases in Ecuador are made through WhatsApp. (CECE, 2020) |
According to the security section of the official WhatsApp website, the payments function allows users to make transfers between bank accounts and other financial institutions. Although sensitive data such as card and account numbers are encrypted and stored on a security network, they cannot be end-to-end encrypted because banks need access to this information to process transactions. Can you imagine what can happen?
Our advice
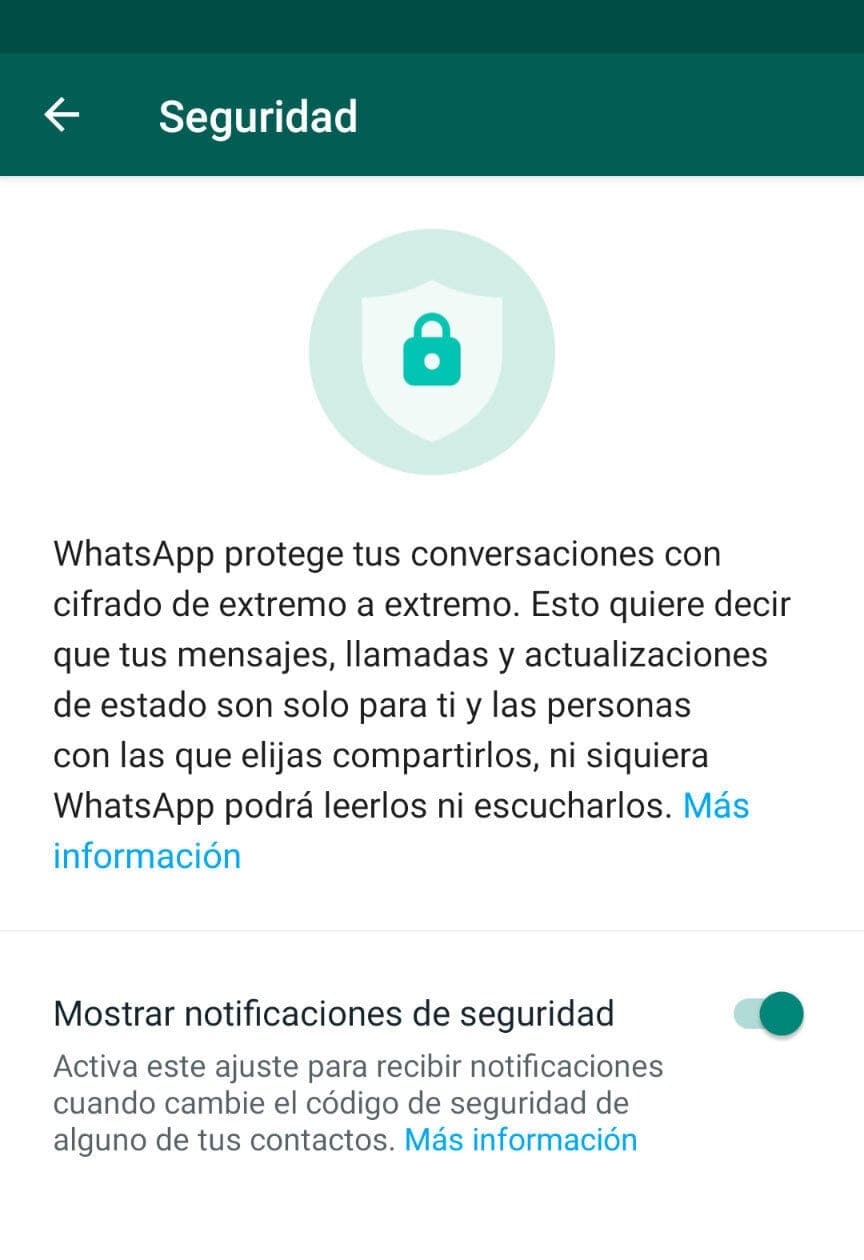
Before starting a new chat, verify that it is end-to-end encrypted by opening the conversation with your contact and tapping on their profile. It also enables WhatsApp security notifications.
Remember that, if you are a victim of a cybercrime, the National Police recommends filing a complaint with the Citizen Services of the Prosecutor's Office.